Business Impact Analysis to Quantify Cyber Threats
Threat modeling is a structured process to identify potential threat sources and the event they may cause on an information system. As such, they aim to help answer the question of “what could go wrong?” and not necessarily “what is wrong in the system?” (vulnerabilities). This distinction is important for cases, where vulnerability assessment is not feasible, realistic, or cost-efficient. Nevertheless, each threat must be evaluated to answer the question “how bad is it if this actually goes wrong?”. Currently, many threat modeling approaches and applications leverage a qualitative approach to assess the impact of threats (e.g., categorizing into low, medium, or high). While this is enough for many cases (e.g., during a short software implementation cycle), a qualitative analysis can hinder communication with non-technical stakeholders – a quantitative approach would allow to translate a threat model into the broader scope of an enterprises' risk management program.
This thesis demands that a methodology (i.e., a clear set of steps that must be followed) is being developed that allows an organization to assess the business impact of a given threat (e.g., ransomware attack or cyber fraud). In a second step, the methodology should be supported by a guiding application, which can be integrated into CoReTM (see Figure 1), an existing threat modeling platform [1].
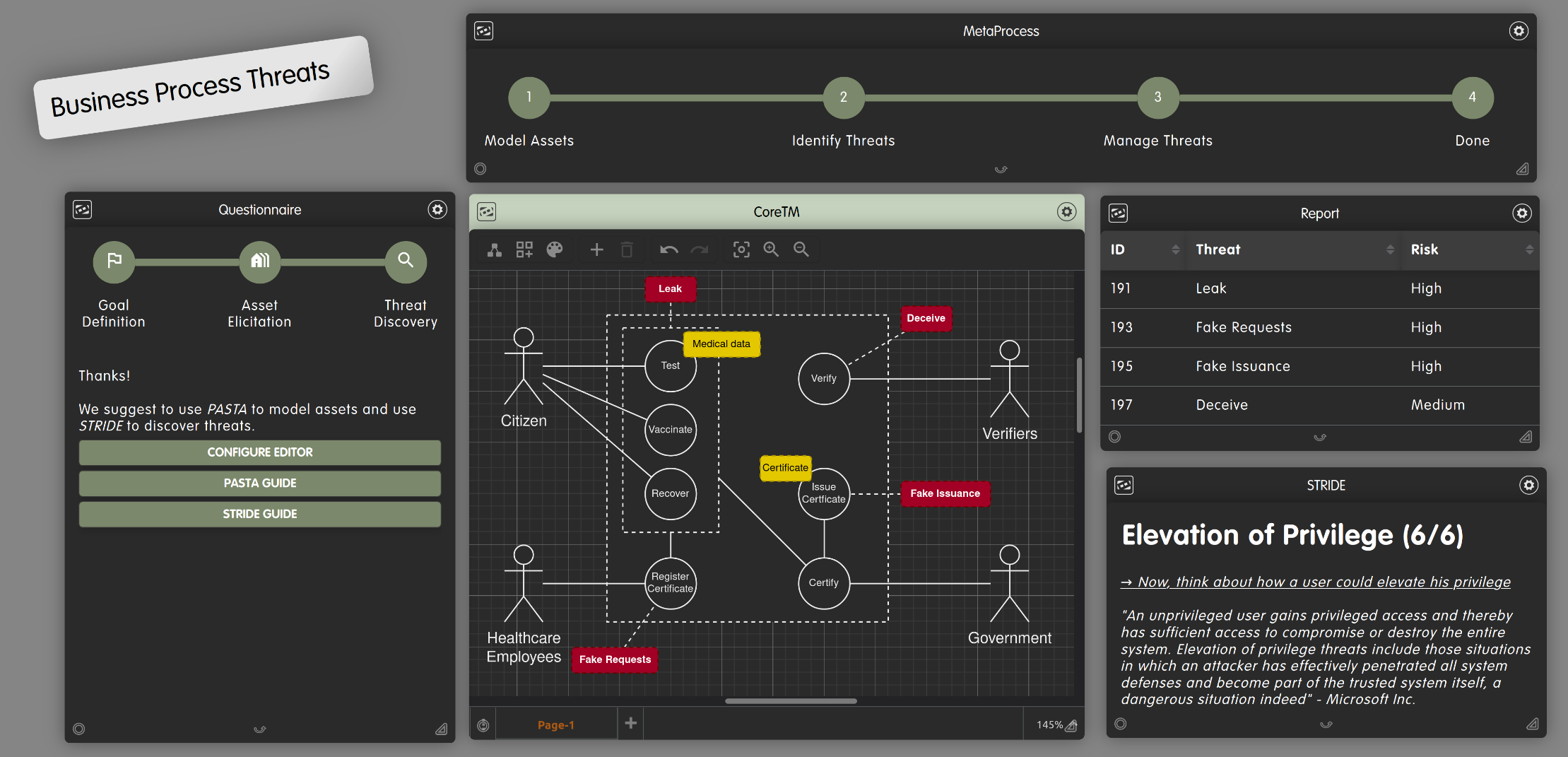 Fig.1 - Creating a Threat Model of a Use Case with CoReTM
Fig.1 - Creating a Threat Model of a Use Case with CoReTM
[1] Jan von der Assen, Muriel F. Franco, Christian Killer, Eder J. Scheid, Burkhard Stiller: CoReTM: An Approach Enabling Cross-Functional Collaborative Threat Modeling; IEEE International Conference on Cyber Security and Resilience, Virtually, Europe, July 2022, pp. 1–8. Available Online
Supervisors: Jan von der Assen
back to the main page