Navigation auf uzh.ch
Navigation auf uzh.ch
Today a growing number of applications within the Internet of Things (IoT) depends on data collected by wireless sensor networks. The individual nodes of these networks have severe resource limitations, concerning storage, processing, and transmission capabilities, but also concerning energy available for communication functions. Supporting the required protocol functionality in combination with the goal of energy-saving operation typically results in the development of proprietary, highly specialized communication protocols for wireless sensor networks (WSN).
However, with Internet technology as the dominating communication paradigm for a wide range of application areas, it became an attractive goal to be able to use Internet protocols (IP) within WSNs. The idea itself is interesting but at the same time challenging, because the commonly used devices in WSNs are very constraint in memory, computational capacity, and power. The most challenging constraints are the first two if more than only data collection and sending should be performed by the devices. RFC 7228 groups the devices into classes depending on their RAM and ROM resources and points out that only devices with more than 10 KB RAM and 100 KB ROM are able to support Internet connectivity and security functions. The latter becomes essential due to the linkage of WSNs to the Internet and the raising concerns of privacy and security by the users, because any kind of collected data includes sensitive information (e.g., ID, address). Thus, WSN solutions must support security solutions beyond efficient data transmission.
The project SecureWSN faces those challenges and develops different solutions for secure and efficient data transmission for WSNs consisting of devices between 10-50 KB RAM and 100-250 KB ROM.
SecureWSN started with the development of an efficient data transmission protocol. Messages within a WSN have in common that they include meta information and measured values at the same time, and are send automatically in a predefined interval. Due to the fact that the message size is very limited (around 102 bytes on MAC layer using IEEE 802.15.4 radio) and costs energy it needs to be efficient. Thus, the PUSH-based Internet Protocol Flow Information Export (IPFIX) protocol from IP networks standardized in RFC 5101 becomes interesting due to its template-based design. In general IPFIX splits messages into Template and Data Records. Template Records include meta information and Data Records the corresponding values. A drawback of IPFIX is the introduction of additional IPFIX headers with around 20 byte size. IPFIX can be used for WSNs in a light-weighted solution together with header compression. TinyIPFIX is the resulting protocol for WSNs including header compression to compress the additional headers down to 3 bytes and reducing redundancy by the re-sending of meta information in each message [2]. The principle is the following: (1) Device boots. (2) Device announces its meta information to the network by sending out a Template Record with unique ID. The Template Record is stored by nodes in the networks (e.g., gateway, aggregator) that need to perform decoding of data (e.g., for aggregation). (3) Now device sends only out Data Records with a reference to the Template Record for decoding purposes. Due to the usage of UDP and especially quick changing topology in the beginning of the WSN establishment the Template Record is re-send periodically. To make proper use of the limited message size TinyIPFIX was extended with aggregation functionality. It can support message aggregation and data aggregation at the same time. The latter is useful in scenarios where pre-processing of data is needed (e.g., control of HVAC system). In order to modify the aggregation type and degree during run-time a SHELL was developed allowing the user to access an aggregator and change the functionality (e.g., MIN, MAX, AVG, degree of aggregation).
In a next step of development SecureWSN faced the security request by the users. Therefore, different security solution where designed and implemented keeping the device resources in mind as well as the idea to re-use standards from IP networks. At the moment SecureWSN supports three security option that have authentication, session key agreement, and being standard-based in common. The TinySAM protocol is a solution developed for devices with 10 KB RAM and max. 100 KB ROM. It offers one-way authentication and works with pre-shared keys. A more secure solution is the developed TinyTO protocol performing the Bellare-Canetti-Krawczyk (BCK) handshake with pre-shared keys resulting in two-way authentication. It uses Elliptic Curve Cryptography (ECC) for key generation, key signatures, and encryption [8]. Where the used 192-bit ECC keys are assumed to be as secure as 1024-2048 bit RSA keys. For devices with more resources the TinyDTLS protocol was designed performing a common DTLS handshake using X.509 certificates and supporting two-way authentication [4].
Beyond the secure and efficient data transmission protocols a graphical user interface (GUI) was design in SecureWSN. Today the users prefer to configure and manage networks in handsome ways usually using buttons. Therefore, the CoMaDa framework was designed, allowing the user to configure, manage, and handling data using an intuitive GUI [5]. CoMaDa works with a virtualization of the deployed WSN and has connection to the deployment via the gateway. The user can program new devices and update running ones, can view the network status, can define how collected data is handled (e.g., stored or forwarded to analysis tools), and receives a visualization of data in raw format and in curve design. The only requirement for CoMaDa is that the user sits directly before his PC, which is connected to the gateway of the WSN. This is a contradiction to the mobility requirement of the user. Thus, WebMaDa was developed and included into CoMaDa [7]. WebMaDa is a Web-based mobile access and data handling framework allowing authorized users to publish their own WSN data online, and grant authorized users (e.g., security firm, fire department) access to the data. Additionally, WebMaDa supports pull requests allowing authorized users to reuqest sensor data independent on the pre-set intervalls used for push process. The pull requests become essential when thinking of emergency requests. Due to limited resources on the sensor node itself, the sensor node answers with a complete data set to the pull request that is filtered based on the set rights of the authorized pull requestor on the CoMaDa part before displaying the measurements on WebMaDa.
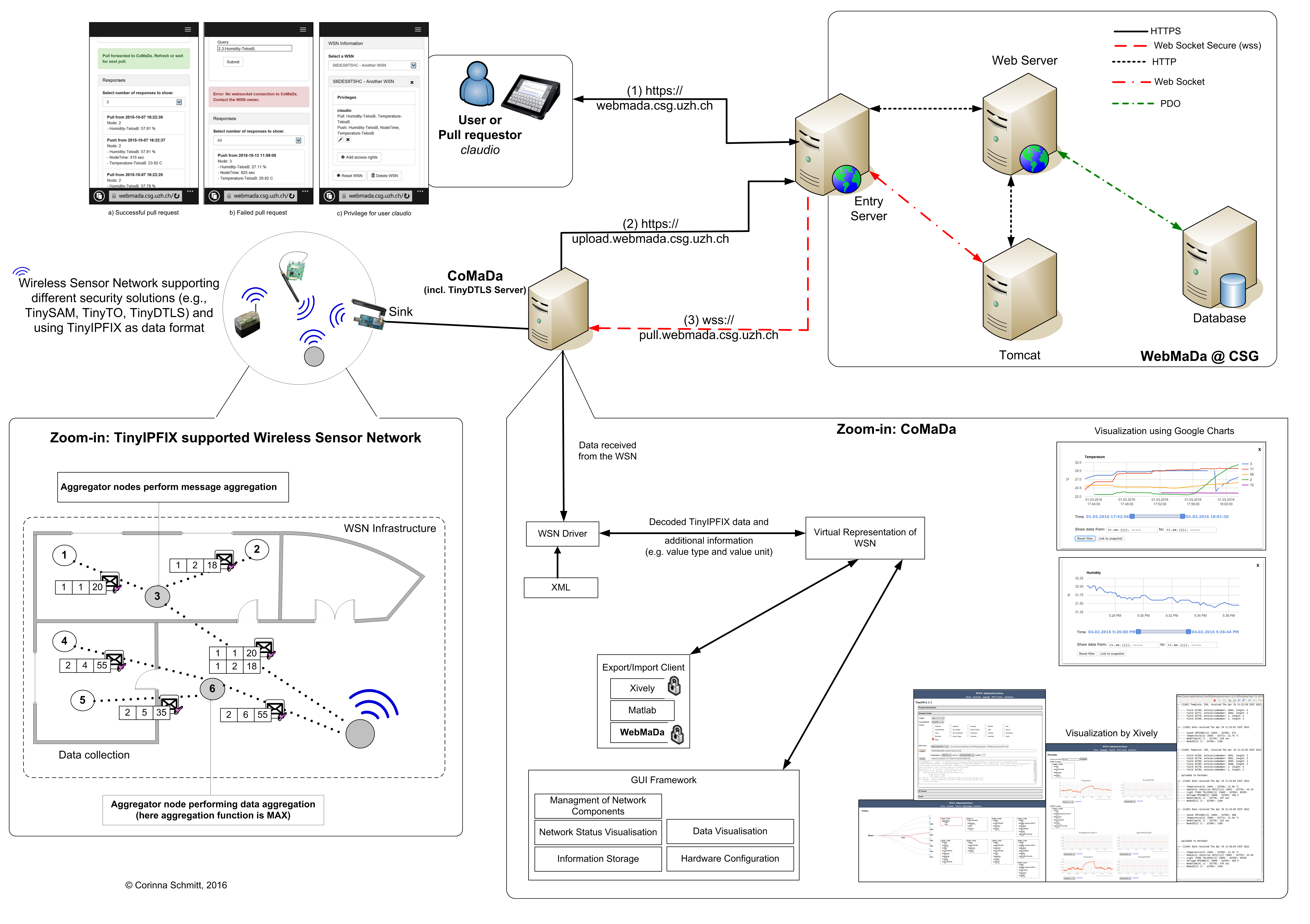
The figure above illustrates the cooperation between all components in the established SecureWSN (status 2015):
Newest features of SecureWSN:
Functional improvement is the goal of this research area that is inspired by questions within the Internet of Things focusing on transmission, trust, and privacy. The solution design has to get along with limited resources on used constraint devices and, thus, it is a challenge.
Topic of interest are not limited to the following ones:
Further information about SecureWSN can be found here.
Inquiries may be directed to:
| Prof. Dr. Burkhard Stiller |
| University of Zürich, IFI |
| Binzmühlestrasse 14 |
| CH-8050 Zürich |
| Switzerland |
|
|
| Phone: +41 44 635 67 10 |
| Fax: +41 44 635 68 09 |